How we Exposed a Terrible VPN provider
Most users define VPN networks as, “Well I dunno I’m too busy making this Bernie meme,” so it’s all too easy to masquerade as a legitimate product. The industry is valued at $25 billion, but when a Google Play Store search turns up VPN providers who don’t know the difference between a proxy and their own damned product, you’ve got to wonder what that $25 billion actually represents.
You hear us talking a lot about spectacular VPNs like ExpressVPN and NordVPN around these parts, but the only reason we can celebrate VPN royalty is that we kiss enough frogs along the way. This story is about one of those frogs, but let’s start where all good stories do, with…
We want to keep the Internet secure, and its inhabitants aware of the quality of the service they choose.
That said, we wouldn’t want to ruin anybody’s hard work. This is why, after much deliberation, we have decided to keep their name private (because even VPNs need security sometimes).
Once Upon a Time…
Once upon a time one of our researchers was out testing VPNs. As you do.
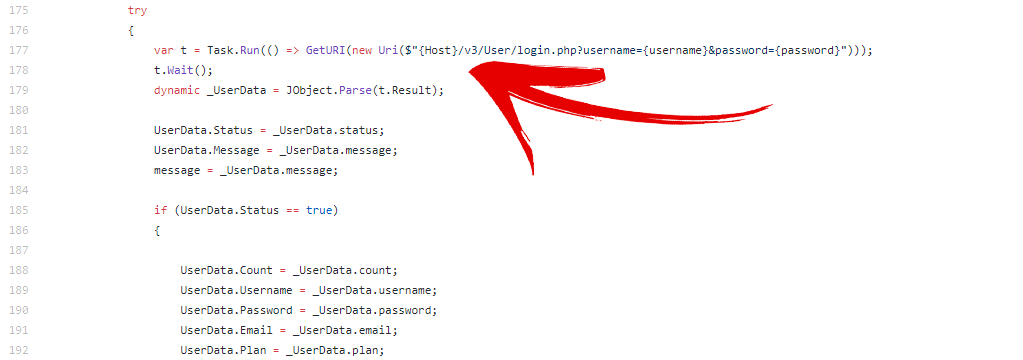
After a while of testing unknown VPN providers, something caught his eye. Being an expert on API (Application Programming Interface) security, he noticed, that one of the providers, that advertised itself as being focused on “bringing the best security, stability, and reliability” as well as offering a “unique service unlike no other“, was using HTTP to send API requests.
To the untrained eye, an HTTP request is just one lowly letter away from an HTTPS, but to pros like our tester, they belong on two different planets.
Why is this bad?
HTTP protocols have no encryption. Zero. Zilch. Nada.
Using unencrypted API requests with your VPN to transfer users’ information is like wearing Bernie mittens to a bank robbery in the hope that they will mask your face. (Hint: they won’t.) This basic encryption protects sensitive information, while simultaneously keeping you safe from online eavesdropping and data theft.
SSL encryption has been around since dinosaurs roamed the interwebs, which is why 50% of the internet is encrypted. It’s one of the most rudimentary protection a VPN can provide. So when it’s missing from a product in the security niche, we tend to notice.
The VPN we’ve tested betrays just about every security standard that makes these products secure. But it’s generous enough to use GitHub published open-source code, so we got to have a long, hard look at our frog under the waterlilies.

GET Requests and No Logging Policies
The VPN in question makes a very bold statement of being a strict no-logging VPN (and here’s where we need to get screamy). You open the provider’s main page, and there it is – staring you down: “No Logs”. Bold claim.
Lots of both high- and low-end VPN providers boast about being true to the no-logs policy. And they generally get away with it, because no-logging is very hard to prove or disprove (until the CIA comes knocking and — Hey! — Here’s everything you need to know, please don’t hurt us). However, they do take steps to keep this information well-hidden. Not this one though.
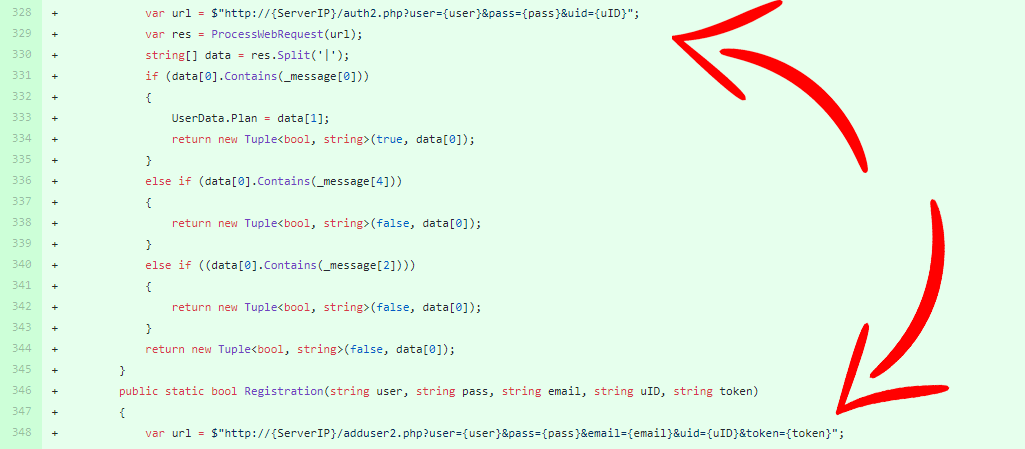
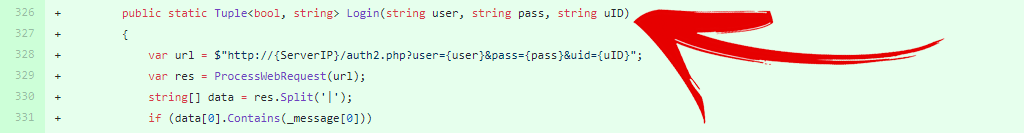
For logging in to the app, this provider uses GET requests (25 billion exclamation points)!
Now, this might sound like nerd gibberish to you (definitely not ALL CAPS worthy), but we will explain why this matters in great detail.
Why is this bad?
There are two kinds of requests for handling data transfers to your server when you log in:
1. POST requests, which don’t log aspects of your digital “fingerprint” like username and passwords.
2. GET requests, which do.
Sending login information using a GET request is very dangerous because with it the log files of the webserver will now contain all of the user’s usernames and passwords. And if it’s there, that means that somebody can get to it — be that the provider, or some cunning hacker.
Whereas with a POST request, this data is never logged.
Not only did this provider’s client send our password and username to the server, but our unique hardware ID, as well. Yep, folks. Our no-logging-policy VPN uses logging policies and my sugar-free post-Christmas diet is made entirely of candyfloss.
If HTTP and GET are bad on their own, their risks are exponentially worse when they’re bundled together. Logging passwords and then transferring that data over unencrypted channels is like posting your banking details on Gumtree.
This VPN might be a virtual network, but it ain’t a private one, and this is where the story gets interesting.
Go ahead and fetch some popcorn. We’ll wait.
The Interesting Part
We feel responsible for making the internet a safer place, so we decided to send our test findings along to the VPN provider. Because we’re nice like that.
In response, they sent us a highly offensive, politically-incorrect ad hominem attack. Because if there’s one universal trait amongst dishonest and un-secure digital products, it’s insecurity.

Why is this bad?
When a company that makes bold security claims is unwilling to consider justified warnings about security holes, this is the last industry it should work in. That kind of bravado isn’t merely unattractive. It’s downright dangerous.
Call it a CyberSecurity version of the Dunning-Kruger Effect if you will.
If you’re new to Dunning-Kruger Effect, psycho-social studies have proven that the less you know, the more certainty you have about your knowledge. When you’re a pro, you have the knowledge required to understand how little you know, but the opposite is true of those who don’t know much.
That’s why rookies often get nasty: Their confidence in their knowledge is built from ignorance.
But there’s a simpler problem to draw from this exchange—the absence of respect for potential customers. If your VPN doesn’t respect you, they won’t respect your security needs either. And this provider most assuredly lacks respect for the GitHub community as well as every client it serves.
This Can’t be a Premium Provider, Right?
If you’re thinking you could spot a Premium VPN-wannabe by its cheap price and cheaper web design, think again.
This provider charges an annual $79,99 and looks every bit as expensive as it is.
Evidently, this provider considers itself at least as good as Surfshark and half as good as, say, NordVPN. Again, pretty bold statement, one that it doesn’t live up to.
So if you’re thinking that half-baked VPNs come free, we urge you to reconsider. They come packed with loud statements and louder prices, and you think you’re paying for quality, while in the meantime you’re being robbed.
The End of the Story
A few days after we checked up on the VPN provider while writing this review. They executed a few surface-level changes to cover up our accusations.
An SSL certificate appeared for their connection and they stopped sending user hardware IDs with everything. We’d give them points for that if they weren’t still using GET requests and making false promises about their logging policy.
Theoretically, they might not be storing data on their servers, but if that’s the case, they wouldn’t have any motivation to use GET requests in the first place. So we’re not falling for it.
The Moral of the Story is…
The world does a lot of handwringing over the information Facebook and Google collect on their users. But then we turn around and hand over our passwords to rooky VPN companies that charge as much as the premium ones.
Most virtual private networks will tell you that even they can’t see what you transmit over the internet, but few actually use the simplest best practices of their industry.
Creating an airtight VPN isn’t complicated. All you need is a dash of willingness, a generous dose of social responsibility, and a ton of professional knowledge.
The provider we’ve tested has none of that, and that could cost its users more than they bargained for.
Alas, not all fairytales end with a handsome prince and a glittering wedding ceremony. Frogs don’t always turn into princes, but that won’t affect you if you stick with us.
We’re way smarter than Prince Charming and just look at our spiffing mittens.





Leave a Reply