
PureVPN leaks DNS
In our recent retesting of PureVPN, we discovered that the provider’s VPN service leaks your DNS requests.
Our recent tests of Pakistani-based PureVPN’s virtual private network service have revealed that the provider’s split tunneling feature leaks the user’s DNS requests. When enabled and applied to be used by web browsers, the feature will expose your DNS requests made through those browsers. This means that PureVPN isn’t sending your DNS requests through the VPN, but directly to your ISP (Internet Service Provider).
This vulnerability could be used by your ISP, as well as potential eavesdroppers and the VPN itself to identify and monitor your destinations on the Internet, which could potentially be a breach of your online privacy and anonymity – something the VPN is meant to uphold.
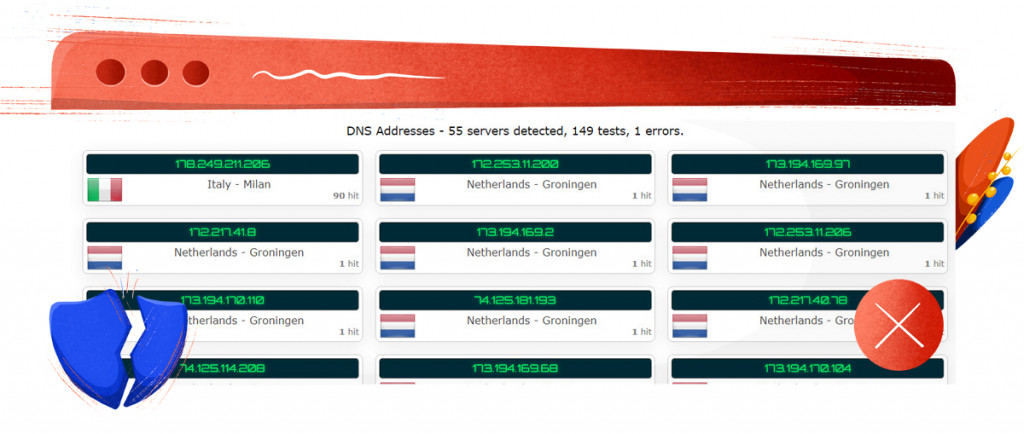
In the past, PureVPN has already had issues with leaking user data. Our initial VPN review has shown that, when enabled, PureVPN’s kill switch feature reestablishes the Internet connection before it restores the VPN tunnel, leaking the user’s real IP address. While this massive privacy risk has seemingly been fixed in PureVPN’s most recent update to their service, the DNS leak has become the provider’s new issue.
DNS leaks have been a known privacy vulnerability with VPNs that feature split tunneling. However, most high-profile VPN providers have been able to fix the issue through many technical possibilities.
A DNS leak occurs when a browser sends DNS requests directly to the Internet Service Provider instead of going through the VPN. This allows the ISP, as well as anyone else on your connection path to see your online destination.
PureVPN has not yet issued a statement in regard to our findings.




Leave a Reply