
Security Flaw Found in Kaspersky Password Manager
Cybersecurity experts from Ledger Donjon found a serious security flaw in Kaspersky’s Password Manager.
The flaw was discovered back in 2019 but made public just now after Kaspersky Lab acknowledged and fixed the issue.
What kind of security flaw are we talking about?
Ledger Donjon’s cybersecurity experts have found out that the passwords that Kaspersky Password Manager was generating only appeared random. In fact, they were created using a pseudorandom number generator and were dependent on the moment the user would click the “Generate new password” button.

This moment, or, to be more specific, the system time (counted in seconds) would become the ‘seed’ number, on the basis of which Kaspersky’s Password Generator would operate.
As a result, if two of Kaspersky Password Manager’s users would generate passwords at the same time while having all of the other settings set to default, the generator would give both of them identical passwords.
Only if the user would choose to change the length of the password, and the characters used, the generator would create a different password.
Here’s how it looked:
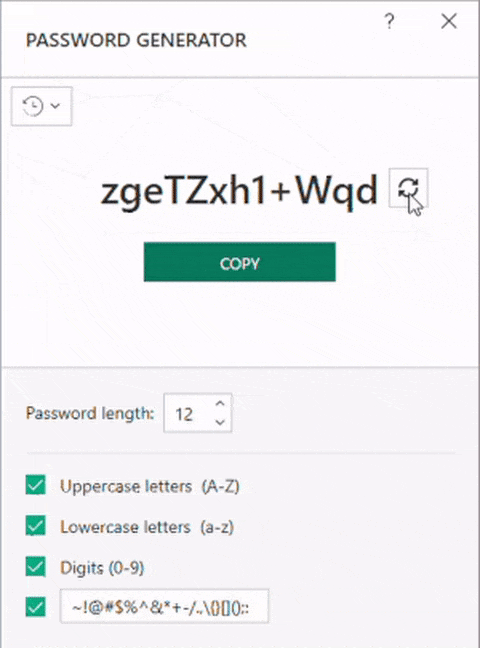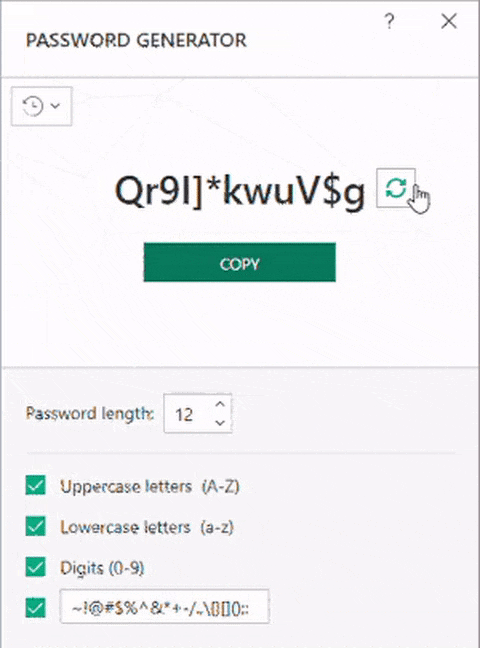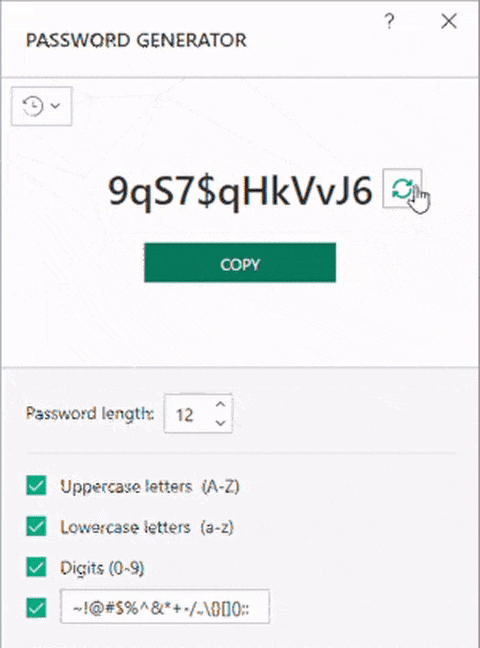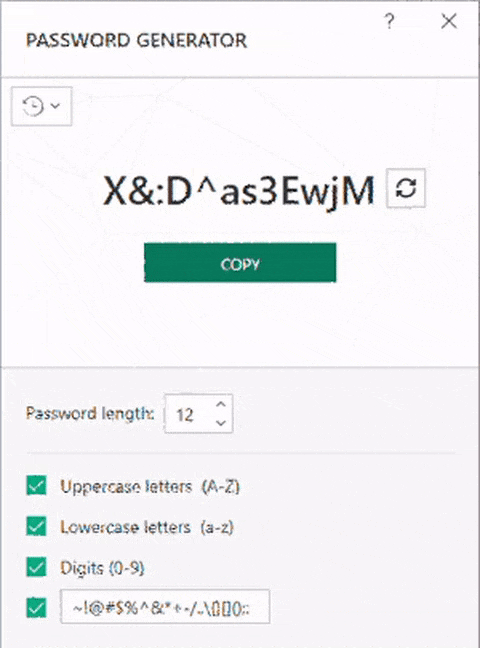
So the problem is that two people might have the same password?
Not exactly, and not only that.
The worst part about this flaw is that in the last 10 years (2011-2012) only 315 million 319 thousand and 200 seconds had passed. This is the exact number of default passwords Kaspersky’s Password Generator could have created since its inception.
People with malicious intent could have easily (using special software for data enumeration) recreated the whole list of Kaspersky-generated passwords. This could have then been used to gain access to archives, devices, documents, bank accounts, hard drives, and so on.

If the potential attacker had the vaguest idea of when the victim had generated the password using Kaspersky’s software, the hack would have been much easier. It would have been possible to recreate the passwords of different lengths and characters (in this case, there are much fewer seed number variants the passwords were based on).
The vulnerability may have remained undetected thanks to the animation that imitated creating a password using random characters. The time it took to generate a password before the user could click the button again took longer than a second.
Even if the user would generate a new password immediately after, the password would have been different.
The user simply had no way of knowing that the software was creating identical passwords.
And this is not the only issue
Generating identical passwords was the main, but not the only problem with Kaspersky’s software.
For one, the pseudorandom number generator the Password Manager was using did not have the features needed to use it in cryptography.
The characters used in the passwords were also not generated with equal probability. Put simply, they were not entirely random.
This may have been used to place the characters more randomly than in actual words. However, if that attacker knew that the victim was using Kaspersky Password Generator, they could have modified their attacks and theoretically recreate the password faster than if the letters, numbers, and characters were completely random.
What should the users of Kaspersky Password Manager do?
If you are using the password manager by Kaspersky Lab, check if you have the versions of the software younger than these ones:
- Kaspersky Password Manager for Windows 9.0.2 Patch F
- Kaspersky Password Manager for Android 9.2.14.872
- Kaspersky Password Manager for iOS 9.2.14.31
If you do, make sure to update your software and definitely change your passwords.





Leave a Reply